Use Credential Injection During Access Sessions
Credentials stored in BeyondTrust Vault can be used to log in to remote systems during support sessions. Ensure the BeyondTrust Vault has been configured and accounts imported or manually added for the representative console to use credential injection.
Credential injection is available for:
- Logging into remote Windows systems
- Answering a UAC prompt
- Running a special action
Credential injection is not available for Mac or Linux Jump Clients.
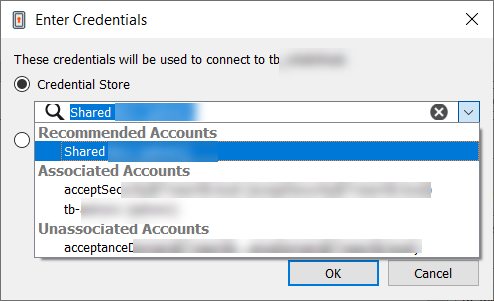
- While in an access console session, you can inject credentials by clicking the key icon.
- A dialog appears, allowing you to click on the dropdown icon to select a credential from the list, or type in part of the account name to filter credentials to select from.
- If multiple accounts have the same name, you can select credential by account (user name).
- Select the appropriate credentials.
The access console retrieves the selected credentials from BeyondTrust Vault and injects them into the session.
For SSH Certificate Authority accounts, the TTL is 5 hours. If you are in a shell jump session that exceeds 5 hours and need to perform an action that requires re-authentication, such as stopping all shells and starting again, the action will fail.
Choose from Favorite Credentials for Injection
After you have used a set of credentials to log into an endpoint, the system stores your preferred credentials for the endpoint and the context in which they were used (to log in, to perform a special action, to elevate, or to push) in the B Series Appliance database. The next time you use a credential to access the same endpoint, the credential injection menu makes a recommendation for which credentials to use. The credentials are displayed at the top of the credentials list, under Recommended Accounts, followed by any remaining credentials. If no credential history exists for an endpoint, the B Series Appliance displays all possible credentials, grouped by accounts that are associated with the Jump Item and not associated with the Jump Item. Jump Item associations for accounts and account groups are configured in /login.
The credential list recommends no more than five credentials.