Use BeyondTrust Vault with Microsoft Entra ID Domain Services Account
Administrators can use Vault to discover and manage Entra ID Domain Services accounts. Managing Entra ID Domain Services accounts requires a service principal, which is defined under the relevant domain in the Vault section of the /login interface.
A service principal must be created in Entra ID before you can add it to the BeyondTrust Vault. Information such as the client secret is obtained from Entra ID when you create the service principal.
Vault cannot be used with Azure domain controllers other than Entra ID Domain Services.
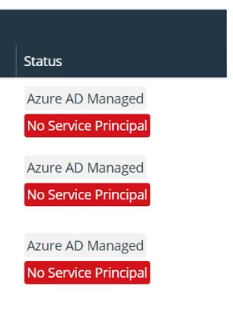
Discovery job results identify Entra ID Managed accounts in the Status column, as well as whether or not the service principal has been added. When the Status displays No Service Principal, the account cannot be selected for import.
For more information on creating a service principal in Entra ID, please see Create a Service Principal in an Entra ID Domain Services Account.
Add or Edit a Service Principal
Adding or editing a service principal can be done before a discovery job, or after a discovery job has identified accounts that require a service principal.
- From the /login interface, navigate to Vault > Domains.
- Scroll down to Microsoft Entra ID Service Principals and click +Add.
- Service principals already added can be edited by clicking the pencil icon at the right end of the row.
- To delete a service principal, click the trash can icon at the right end of the row. The deletion request must be confirmed.
Deleting a service principal deletes all associated accounts.
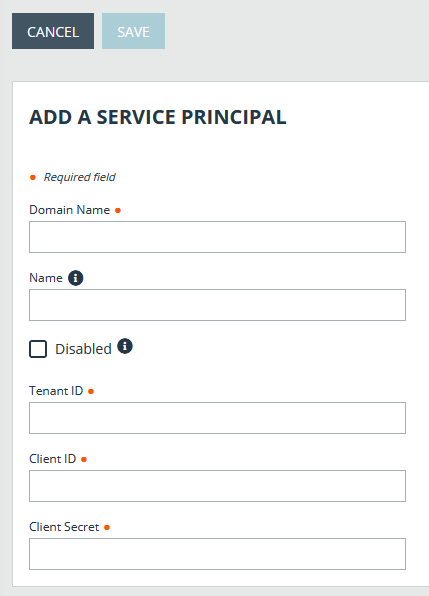
- Enter the mandatory information:
- Domain Name
- Tenant ID
- Client ID
- Client Secret
- If desired, enter a name to easily identify the service principal.
- The service principal can be disabled. This does not remove it, but no actions, such as rotation, can be taken with the account. In the list of discovery results, the account Status is Service Principal Unavailable and Disabled.
- Click Save. Service principal details are validated against the details in your Entra ID tenant.
- If adding the service principal is successful, the new service principal displays in the list of domains, with the status OK.
- If adding the service principal fails, the status is Disabled and Failed. Click the pencil icon to return to the edit screen, and review the detailed error message.
- Run a discovery job again. In the list of results, the account Status is still Entra ID Managed, but the No Service Principal note does not display. The account can now be selected for import.
If the account is a shadow account, the Status displays "Externally Sourced," and the account is not available for import.
- If you have multiple domains for the Entra ID Domain Services instance, repeat the process of adding a service principal for each domain.
On the edit screen for an imported Entra ID account, Entra ID Managed displays at the bottom of the screen.
Rotation, credential injection, and other actions are managed as for other accounts.
Using BeyondTrust Vault with Microsoft Entra ID Domain Services Account requires both an Entra ID license and an Entra ID Domain Services license.
For more information, please see the following: