Policy File Format
In most cases, the order of the instructions in a security policy file is not important. The user’s security requirements determine the rules that the file contains.
User-Written Functions and Procedures
To help simplify security policy implementation, the Endpoint Privilege Management for Unix and Linux Security Policy Scripting Language enables the security administrator to write custom functions and procedures (that is, user-written functions and procedures).
For the remainder of this discussion, the term "function" refers to both user-written functions and procedures. The differences between the two are discussed in Functions and Procedures.
Think of functions as stand-alone units of security code that perform specific programming tasks. After a function is written, the function can be invoked from within any security policy file to perform its specific task or function. It is a good idea to write functions for repetitive programming tasks. Doing so enables the policy instructions to be written once and utilized in multiple places.
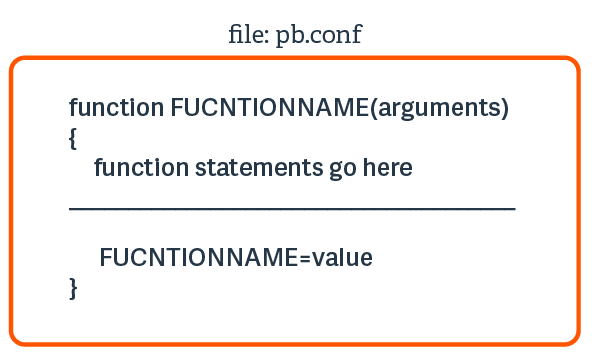
Another benefit of using functions is that any needed changes can be made in only one place. By centralizing the logic for a repetitive type task in one place (that is, a single function), all of the security policy files that call the function automatically benefit from any updates that are made to the function. The following figure illustrates the basic structure of a function.
When a user-written function is used within a security policy file, the code for that function is placed at the top of the security policy file that first references it. In other words, the overall structure of a security policy file is all user-written functions first, followed by security policy code.
A good way to manage and organize user-written functions is to logically group all functions that perform similar types of tasks in a security policy file. Now, add include statements for each of these sub files to the beginning of the pb.conf file. These include statements should come before anything else. When this is done, the functions that are contained within these sub files can be called from within any security policy file.
For more information on creating functions and procedures, see Functions and Procedures.