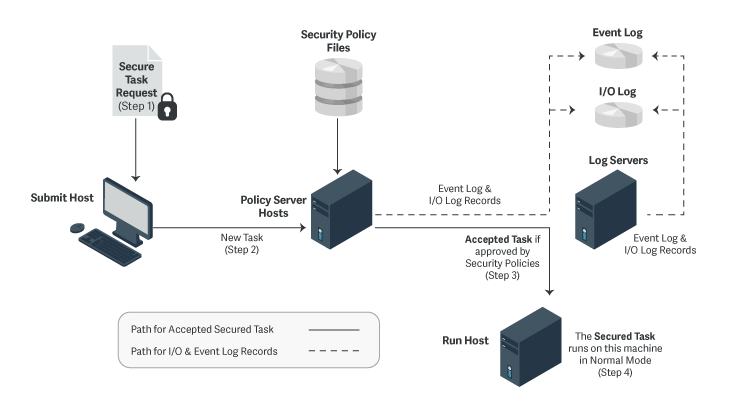
Normal Mode Processing
As shown in the following figure, in normal mode, the machine from which a task is submitted is referred to as the submit host. The machine on which security policy file processing takes place is referred to as the policy server host. The machine on which a task is actually executed is referred to as the run host. The machine on which event log records and I/O log records are written is referred to as the log host. Use of the log server daemon pblogd is optional, but highly recommended.