Optional Event Centralization Configuration
Optimize Event Forwarding
Forwarder Resource Usage
It is possible to control the volume of events sent to the event collector by the source computer. This may be required in high volume environments.
The following Group Policy settings are used to configure Forwarder Resource Usage:
- Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding\ForwardResourceUsage
This GPO controls resource usage for the forwarder (source computer) by controlling the events per second sent to the event collector. This setting applies across all subscriptions for the forwarder (source computer).
Reduce the TCP/IP Connection Idle Time
A Windows Server is capable of 16,000 concurrent TCP/IP connections; if your environment has more than 16,000 source computers connected to an event collector, not all the machines are able to communicate at the same time. In large enterprise environments where large numbers of source computers are required to connect to an event collector, we recommend reducing the TCP/IP idle time to improve the speed at which source computers can connect.
It is possible to connect about 100,000 source computers to a single event collector. However, in this scenario, Microsoft recommends setting the TCP/IP idle time to 2 minutes.
- Open an elevated command prompt on the event collector.
- Enter net config server /autodisconnect:2
- The message command completed successfully should be displayed.
The purpose is to disconnect idle sessions after a set number of minutes. The valid value range is -1 to 65535 minutes. To disable Autodisconnect set it to -1.
Setting Autodisconnect to 0 does not turn it off and results in very fast disconnects, within a few seconds of idle time. However, the RAS Autodisconnect parameter is turned off if you set it to a value of 0.
Event Log Retention
The forwarded events log must be set to a size large enough to ensure the log does not wrap before the data is parsed into BeyondTrust’s Endpoint Privilege Management Reporting database or upstream event collectors.
The theoretical maximum log file size for the forwarded events log on Windows Server 2008 R2 is 2 terabytes. However, as the log file grows, the Event Viewer UI takes longer to load and show results for custom views. Depending on the size of the network, a 1GB forwarded events log file can hold from a few hours to a few days’ worth of log data. Due to this size limitation, review the log regularly and set up the appropriate size for your environment.
The above information is intended for the server acting as the event collector. The size of the event log on the source computers is less critical, however if the event collector is unavailable, events are collected locally and forwarded once the event collector is back online. Therefore, we recommend considering the impact of offline event collectors and set the size of the client machine event log accordingly.
BeyondTrust’s Professional Services team can provide best practice advice in this area.
Configure the Event Collector Service with Group Policy
Group policy may be used to enable and configure Windows Remote Management (WinRM). This section focuses on configuring the WinRM service to listen for incoming events. This can be configured with the following Group Policy setting:
- Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Remote Management\WinRM Service\
When editing Group Policy settings, ensure the event collectors are under the management scope of the Group Policy Object being editing.
- Edit the Group Policy Object (GPO) being used.
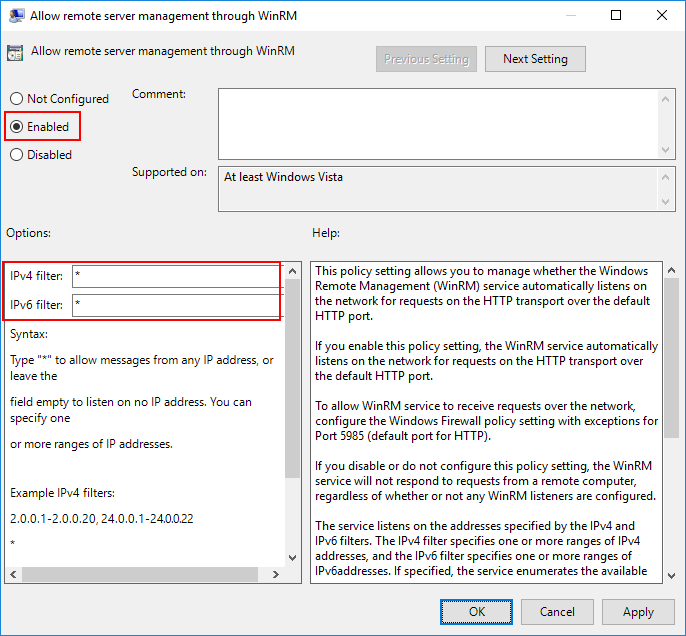
- Navigate to ./Allow remote server management through WinRM (see above for full path).
- Select Enabled.
- Specify * as the filter.
This Listener configuration should only be used in a trusted network environment. If the environment is not trusted (like the internet), then configure only specific IP addresses or ranges in the IPv4 and IPv6 filters.
If you are using Windows Server 2008 R2 as the event collector or have upgraded to Windows Remote Management 2.0 (which is recommended), then you will need to enable Compatibility mode to receive events from down-level clients. The following Group Policy settings are used:
- ./Turn on Compatibility HTTP Listener
- ./Turn on Compatibility HTTPS Listener
Configuration Steps:
- Navigate to ./Turn on Compatibility HTTP Listener (see above for full path).
- Select Enabled.
- Navigate to ./Turn on Compatibility HTTPS Listener (see above for full path).
- Select Enabled.
winrm set winrm/config/service @{EnableCompatibilityHttpListener="true"}Specify the Event Collector Server Address Port with Group Policy
The event collector’s server address port can be configured with Group Policy. To do this, the full URI must be specified within the address configuration of the following GPO settings:
- Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding\
WinRM 2.0 Settings
- Server=http://<Event Collectors FQDN>:5985/wsman/SubscriptionManager/WEC
- Server=https:// <Event Collectors FQDN>:5986/wsman/SubscriptionManager/WEC
WinRM 1.1 Settings
- Server=http://<Event Collectors FQDN>:80/wsman/SubscriptionManager/WEC
- Server=https://<Event Collectors FQDN>:443/wsman/SubscriptionManager/WEC
The syntax used here depends on the WinRM version running on the event collector and whether HTTP or HTTPS is used. If HTTPS is used, a valid SSL certificate is needed.
Additional information may be configured. The syntax of the SubscriptionManagers value is:
Server=[http|https]://HOSTNAME[:PORT][/wsman/SubscriptionManager/WEC[,Refresh=SECONDS][,IssuerCA=THUMBPRINT]]
Each option for the SubscriptionManager is a comma-delimited string containing the following parts:
- Server: FQDN or Hostname
- Refresh: The number of seconds to send events to the server
- IssuerCA: Thumbprint of the client authentication certificate
For more information on how to configure WinRM to use SSL certificates, see https://docs.microsoft.com/en-us/windows/win32/wec/setting-up-a-source-initiated-subscription.
Configure WinRM Enhanced Security with Group Policy
The security configuration is divided into two parts: service and client. The service configuration manages the WinRM service that receives WS-Management requests from clients.
The following are supported authentication methods:
- Basic Authentication
- Digest Authentication
- Credential Security
- Support Provider (CredSSP)
- Negotiate Authentication
- Kerberos Authentication
- Client Certificate-based Authentication
- Channel Binding Token
The security settings must be compatible between the client and the service. The following Group Policy settings may be configured for the WinRM Client and Service:
Computer Configuration/Policies/Administrative Templates/Windows Components/Windows Remote Management/WinRM Client/
Computer Configuration/Policies/Administrative Templates/Windows Components/Windows Remote Management/WinRM Service/
It is important these settings are compatible with your operating environment and the WinRM Client and WinRM Service settings are compatible. Misconfiguration may stop WinRM from operating correctly.
Allow Basic Authentication
This policy setting allows you to manage whether Windows Remote Management (WinRM) uses basic authentication. If you enable this policy setting, then WinRM will use basic authentication.
If WinRM is configured to use HTTP transport, then the user name and password are sent over the network as clear text.
Disallow Digest Authentication
This mode of authentication is a challenge-response scheme. The client will initiate the request, and in response, the server will send a server-specified token string to the client. After the token string is received, the client will append the resource request with the user name of the client, the hash of the user name’s password, and the token string to the response message.
This method of authentication is abused by attackers using a technique called Pass the Hash. Pass the Hash is a way for an attacker to use the password hashes to authenticate as the user without ever discovering the user’s actual password. The client has the option to set Digest Authentication, while the service does not. Additionally, the service can allow hardening of WinRM TLS connections using channel binding tokens.
Allow Credential Security Support Provider Authentication (CredSPP)
This policy setting allows you to manage whether Windows Remote Management (WinRM) uses CredSSP authentication. CredSSP provides a secure way to delegate a user’s credentials from a client to a target server. The SSP provides the capability of Single Sign-on (SSO) in Terminal Services sessions. This option is only available for WinRM 2.0.
Disallow Keberos Authentication
Kerberos version 5 is used as a method of authentication and communication between the service and client. This policy setting allows you to manage whether Windows Remote Management (WinRM) will not use Kerberos authentication directly.
If you enable this policy setting, then WinRM will not use Kerberos authentication directly. Kerberos may still be used if WinRM is using the Negotiate authentication and Kerberos is selected.
Disallow Negotiate Authentication
Negotiate authentication is a Security Support Provider (SSP) that provides a client with two alternative methods for authentication: Kerberos and NTLM. This policy setting allows you to manage whether Windows Remote Management (WinRM) will not use Negotiate authentication. Negotiate will initially select Kerberos as the default; otherwise, NTLM is used.
Disabling Negotiate authentication may result in unforeseen problems when trying to configure WinRM locally. When the remote destination is the local host and the client is in the domain, WinRM uses Negotiate authentication. If an error arises stating Negotiate authentication is disabled, a workaround is to use Kerberos locally by specifying the local host name in the remote switch. Setting the Disallow Negotiate Authentication policy to Enabled is recommended.
Allow Unencrypted Traffic
This policy setting allows you to manage whether Windows Remote Management (WinRM) sends and receives unencrypted messages over the network. If you enable this policy setting, then WinRM sends and receives unencrypted messages over the network.
Trusted Hosts (Client Only)
Trusted host authentication is used for computers not using HTTPS or Kerberos for authentication. A list of computers (non-domain members) can be provided and marked trusted. If you enable this policy setting, the WinRM client uses a specified list to determine if the destination event collector is a trusted entity. These computers, when using WinRM, will not be authenticated.
Specify Channel Binding Token Hardening Level (Service Only)
A common threat amongst NTLML, NTLMv2, and Kerberos authentication methods is a Man-in-the-Middle (MitM) attack. Channel Binding Token (CBT) authentication option involves securing communication channels between a client and server using Transport Layer Security (TLS).
A MitM attacker is positioned between a client and a server to impersonate as both the server and client. When the client initiates a request to the server, the attacker captures the client’s first request and forwards it to the server on the client’s behalf. The server responds with an authentication request. The attacker receives the server’s request and forwards the request to the client. When this request is received by the client, the client sends their credentials as a response. As previously done, these credentials are sent to the attacker because the client assumes it is communicating with the server and now the attacker can access the resource. CBT ensures a secure communication channel with the client. If a MitM is underway, then the two connections will generate two different tokens (sessions in particular; server-to-attacker and client-to attacker). When the CBT-aware server notices this discrepancy, it will refuse the authentication request.
Channel Binding Tokens can be set to:
- None: Not using any CBTs
- Relaxed: Any invalid tokens are rejected, but any channel without a binding token will be accepted
- Strict: Any request with an invalid channel token is rejected
If Hardening Level is set to Strict, any request not containing a valid channel binding token will be rejected. This option is only available for WinRM 2.0.
Disable Windows Remote Shell
When WinRM completes execution of quickconfig, Windows Remote Shell (WinRS) will be enabled by default and will accept connections. This poses a potential security risk and you may want to disable this. If the Windows Remote Shell service is needed for a task, temporarily enable it and then disable it when the task is completed.
WinRS can be disabled for domains using Group Policy. This policy enforcement applies for the collector and sources in the domain. WinRS policies can be found by navigating to:
- Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Remote Shell\
To disable WinRS:
- Set the Allow Remote Shell Access policy to Disabled.
- Click OK.
WinRS can also be disabled by using the command line:
winrm set winrm/config/winrs @{AllowRemoteShellAccess="false"}]
| Parameters | Description |
|---|---|
| AllowRemoteShellAccess | Permit remote shell access. |
| IdleTimeout | The time, in milliseconds, before a shell connection is terminated. |
| MaxConcurrentUsers | Maximum number of users that can request shell access at one time. |
| MaxShellRunTime | Maximum duration, in milliseconds, that command can run for. This value is not configurable in WinRM 2.0. |
| MaxProcessesPerShell | Maximum number of processes that a single shell can create. |
| MaxMemoryPerShellMB | Maximum amount of memory that a single shell can use. |
| MaxShellsPerUser | Maximum number of shells a user can create. |
Client Certificate-Based Authentication
The WinRM traffic between the collector and source is encrypted using a Windows Integrated Authentication or HTTPS. The message payload of the WinRM traffic is encrypted using one of the three authentication methods provided by Integrated Windows Authentication: Negotiate, Kerberos, or CredSSP.
WinRM with SSL requires certificates to authenticate the collector and source. Services can verify the connecting client’s authenticity by examining its certificate. If the authentication process fails, then the client’s connection is revoked.
The general steps consist of configuring the listening port, creating certificates for collectors and sources, configuring the subscription manager, creating certificates, and configuring subscriptions.
There is no Group Policy setting to disable Certificate-Based Authentication for WinRM’s client configuration. The only alternative is using the command line:
winrm set winrm/config/client/auth @{Certificate="false"}
Configuring Windows Event Forwarding to use HTTPS is beyond the scope of this document. BeyondTrust’s Professional Services team can provide advice and assistance in this area if required. Please contact your account manager for more information.
Restrict WinRM Access
The default rules permit connections from any IP address to the specific WinRM port. An attacker who has presence on a network can possibly access machines and servers by accessing WinRM services. This attack can be mitigated by customizing firewall rules to only allow connections between collectors and sources.
These configurations apply to the WinRM predefined firewall rules under:
- Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Inbound Rules
Event Source Firewall Modifications
To enable WinRM firewall rules on the sources:
- Right-click the predefined WinRM firewall rule and select Properties.
- Navigate to the Scope tab.
- In the Remote IP Address area, select the These IP addresses option.
- Click the Add… button.
- Select the This IP address or subnet option and enter the IP address of the collector.
- Click OK.
This assumes the Microsoft Windows Firewall is being used.
Collector Firewall Modification
Repeat the steps for the predefined WinRM rule at Configure Event Collection Services and Windows Firewall.
We recommend setting the Predefined set of computers option to Local subnet. This rule can be changed to best suit your environment.
Raise Actions and Tasks Based on Collected Events
In many situations, administrators or security professionals may want to be informed when a particular event is collected. It is possible to trigger the following actions by assigning a task to be in the event collector’s forwarded events log:
- Start a program
- Display a message
For example, an administrator may want to be informed by email when a user has elevated an application using the On-Demand facility (Event ID 101).
- Open the Event Viewer utility on the Event Collector.
- Right-click on the Forwarded Events log and select Attach a Task To this Log.
- Give the Task a name and click Next.
- Click Next.
- Select the Action required.
- Complete the action details and click Next.
- Click Finish. The task is now set up.
Advanced Options
It is possible to set advanced configuration options and filters by reviewing the action for the Windows Task Scheduler > Event Viewer Tasks: