Manage EPM-UL Role-Based Policies
Role-based policy management is disabled on hosts configured to use script-based policy. For more information, see Role-Based vs. Script-Based Policies.
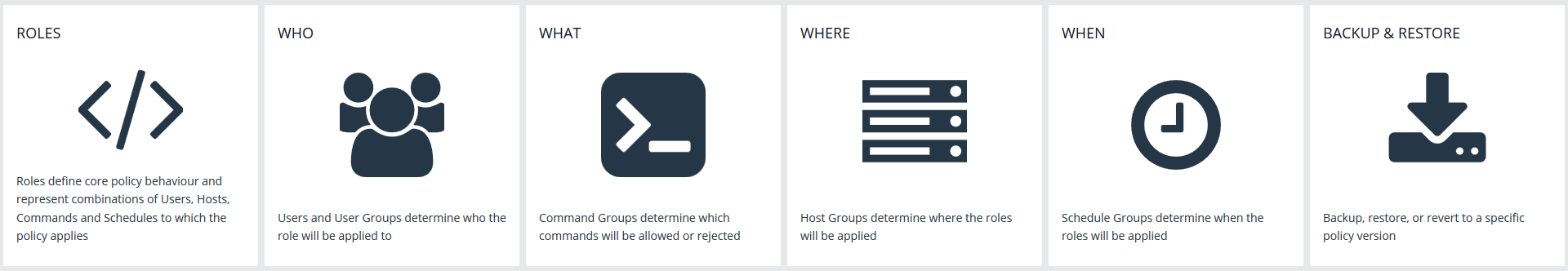
an Endpoint Privilege Management for Unix and Linux (EPM-UL) role-based policy defines which users can use commands and when they can perform these actions on hosts. These role entities are then associated to a role. A User, Host, Command, and Schedule entity can be used in multiple roles, allowing the user to create a single definition and share it. The role-based policy editor is divided into sections allowing for the management of roles and each of the role entities.
Choose the EPM-UL role-based policy option and an appropriate policy server from the selection lists to load the Role Based Policy menu.
Fields may be disabled during policy configuration when the options are not available for the installed version of EPM-UL.
Entitlement Reporting
EPM-UL hosts running 10.1 and later in Role Based Policy Mode can take advantage of Entitlement reporting to discover who is able to do what, where, and when.
Entitlement reporting can be enabled per policy or to all role-based policies.
A default value for reporting can be configured in Settings; if enabled, all new role-based policies defaults to entitlement reporting enabled, or vice versa if set to false. Additionally, this setting can be locked so the default value is both set and unchangeable per policy. This is for new policies only; disabling entitlement reporting does not change the values for existing policies.
For more information, see the following: