Manage File Integrity Monitoring Policies
Create file integrity policy definitions to monitor for file changes. A policy definition includes a target that identifies the type of object that you want to monitor. Some of the target types include directory, device, symbolic link, script, and executable.
You can assign attributes to the target type. An attribute is an action you want to monitor and includes the following examples:
- File moves
- File ownership changes
- Date and time changes
A policy definition can contain more than one target.
Create a FIM Policy
To create a FIM policy:
- On the Home page, click Policy Management.
- Using the filtering options (or from the list), select a server.
- At the right of the server hostname row, click the vertical ellipsis menu icon, and then select FIM.
- Click Policies.
- At the right, click Create New FIM Policy.
- In the Create New Policy panel, and enter a name for the policy.
- In the Change requested by [loggedInUserName] field, enter a reason for the change.
- Click Create.
To create a FIM rule for the policy:
- In the list, click the Policy name you have just created.
- On the Policy Details page, at the right, click Add New FIM Rule.
- In the Create new FIM rule panel, enter a Rule name.
- In the Change requested by [loggedInUserName] field, enter a reason for the change.
- Click Create.
To delete a FIM Rule, click the appropriate FIM policy to navigate to Policy Details > Rules. Click the trash bin icon to delete the FIM Rule for the policy.
To add a FIM target:
- On the Policy Details page, click on the rule name you have just created.
- On the Rule Definition Editor page, click Add New FIM Target to add a target to the definition.
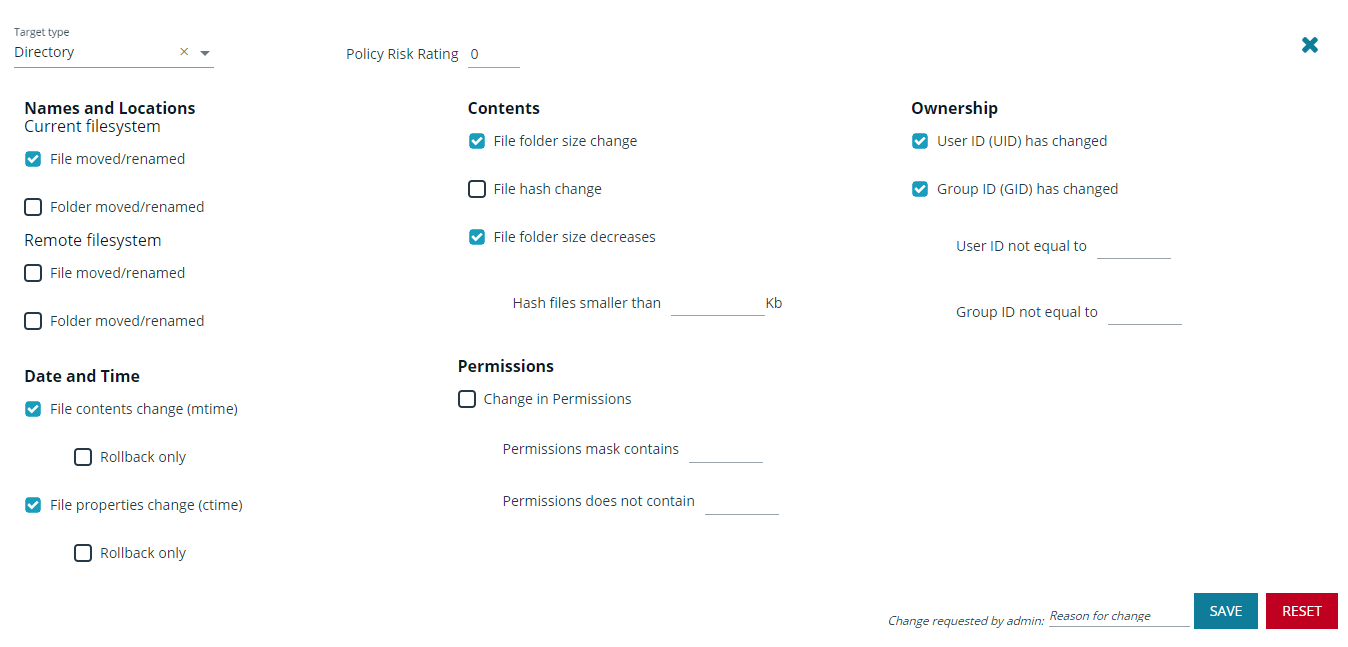
- Select a Target type, and then set attributes you want to monitor.
- You can assign a policy risk rating. The accepted values are between 1 to 10. A risk rating weighs the severity of the monitored actions configured for the targets.
- In the Change requested by [loggedInUserName] field, enter a reason for the change.
- Click Save.
- On the Policy Details page, click on the rule you just created.
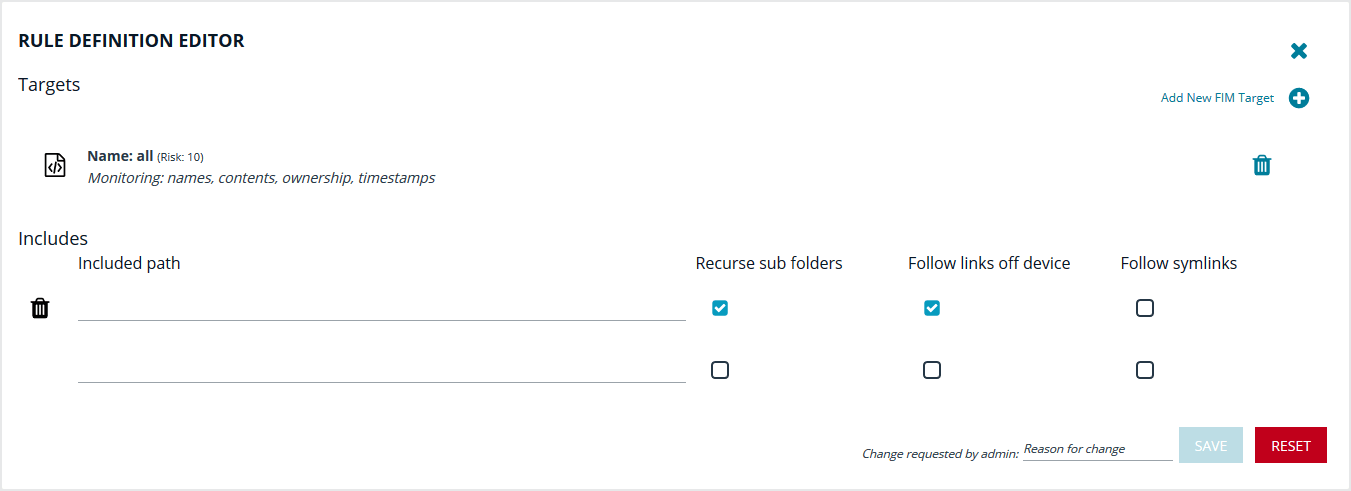
- On the Rule Definition Editor page, enter Included path entries. Optionally, check the boxes:
- Recurse sub folders
- Follow symlinks
- Follow links off device
The policy applies to all files in the path.
- In the Change requested by [loggedInUserName] field, enter a reason for the change.
- Click Save.
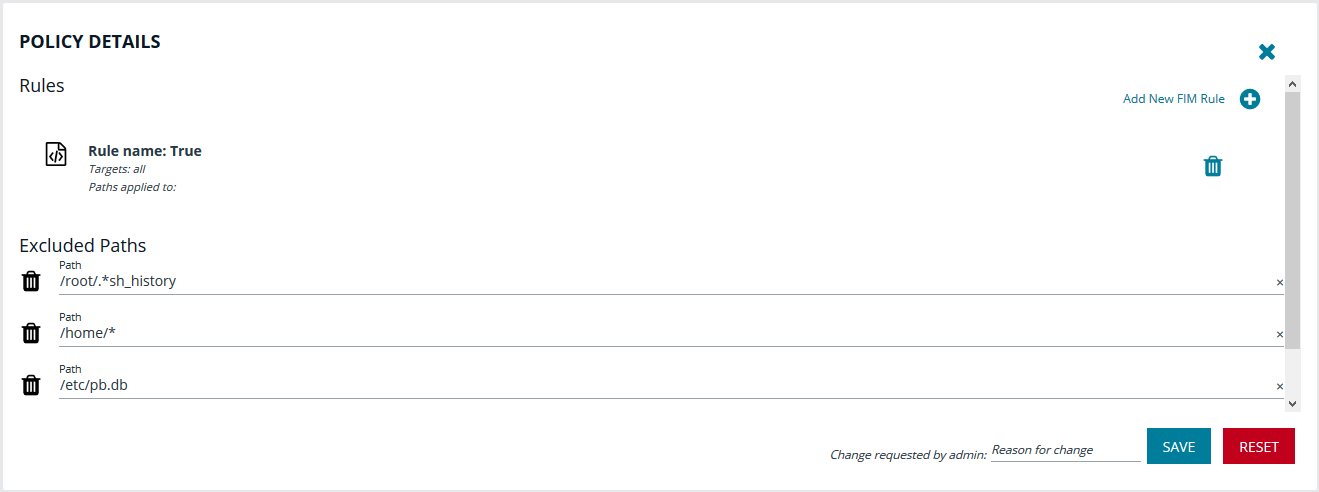
- In the Exclude Paths section, enter paths that you do not want to monitor.
- In the Change requested by [loggedInUserName] field, enter a reason for the change.
- Click Save.
Clone a FIM Policy
You may want to clone a policy in order to make a backup, or use it as a template to create a new one. On the File Integrity Monitoring page, select the clone icon on an existing policy, enter a unique Policy name, and click Clone.
Each policy requires a unique name. In order to clone a policy, you must give it a new name; otherwise, the Clone button does not activate.
Delete a FIM Policy
To delete a FIM policy:
- Go to the Policy Management page.
- Using the filtering options (or from the list), select a server.
- At the right of the server hostname row, click the vertical ellipsis menu icon, and then select FIM.
- Click Policies.
- In the FIM Policies list, click the trash bin icon at the right of the policy you want to remove, and then click Delete to confirm.