Examples
From the Password Safe API Guide:
GET AccessLevels
Purpose
Returns a list of access levels for permissions, for example, None, Read, and Read/Write.
Required Permissions
User Accounts Management (Read).
Request Body
None.
Response Body
Content-Type: application/json
[
{
AccessLevelID:int,
Name: string,
},
…
]
Response Codes
200 - Request successful. Access Levels in the response body.
For more information, please see Common Response Codes.
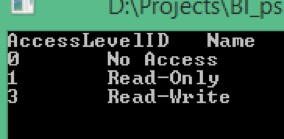
Here's how to issue this API via PSRUN:
psrun2 127.0.0.1 3ea6..acb5acc cli GET AccessLevels
By default, results are tab-separated.
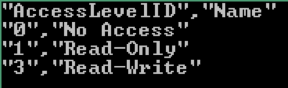
You can change this behavior to get CSV output:
psrun2 -quote -separator "," 127.0.0.1 3ea6..acb5acc cli GET AccessLevels
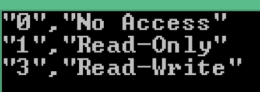
It is also possible to remove the headers:
psrun2 -quote -separator "," -noheaders 127.0.0.1 3ea6..acb5acc cli GET AccessLevels
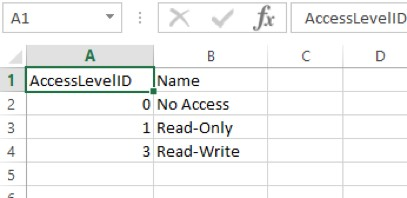
You can export the results through redirection:
psrun2 127.0.0.1 3ea6..acb5acc cli GET AccessLevels > results.xls
psrun2 -quote -separator "," 127.0.0.1 3ea6..acb5acc cli GET AccessLevels > results.csv
The results can be viewed in Excel.
POST Requests
Purpose
Creates a new release request.
Required Roles
- Requestor or requestor/approver role to managed account referenced by ID
For information on ISA role access, please see ISA Requests.
Request Body
Content-Type: application/json
{
AccessType: string,
SystemID: int,
AccountID: int,
ApplicationID: int, // can be null
DurationMinutes : int,
Reason : string,
AccessPolicyScheduleID : int, // can be null
ConflictOption : string,
TicketSystemID : int,
TicketNumber : string,
RotateOnCheckin: bool
}
Request Body Details
- AccessType: (optional, default: View) The type of access requested (View, RDP, SSH, App).
- View: View Password access.
- RDP: RDP access (corresponds to POST Sessions SessionType RDP or rdpfile).
- SSH: SSH access (corresponds to POST Sessions SessionType SSH).
- App: Application access (corresponds to POST Sessions SessionType App or appfile).
- SystemID: (required) ID of the managed system to request.
- AccountID: (required) ID of the managed account to request.
- ApplicationID: (required when AccessType=App): ID of the application for an application-based request.
- DurationMinutes: (required: 1-525600) The request duration (in minutes).
- Reason: (optional) The reason for the request.
- AccessPolicyScheduleID: (optional) The schedule ID of an access policy to use for the request. If omitted, automatically selects the best schedule.
- ConflictOption: (optional) The conflict resolution option to use if an existing request is found for the same user, system, and account (reuse, renew). If omitted and a conflicting request is found, returns a 409 code (see below).
- reuse: Returns an existing, approved request ID for the same user/system/account/access type (if one exists). If the request does not already exist, creates a new request using the request body details.
- renew: Cancels any existing approved requests for the same user/system/account and creates a new request using the request body details.
- TicketSystemID: ID of the ticket system. If omitted, then default ticket system will be used.
- TicketNumber: Number of associated ticket. Can be required if ticket system is marked as required in the access policy used. Max string length is 20.
- RotateOnCheckin: (optional, default: true) True to rotate the credentials on check-in/expiry, otherwise false. This property can only be used if the access policy (either auto-selected or given in AccessPolicyScheduleID) supports it.
In reference to RotateOnCheckin, If the Managed Account given in AccountID does not rotate the credentials after check-in/expiry, this setting is ignored.
For more information, please see the Allow API Rotation Override access policy setting under View access.
Response Body
{
RequestID: int
}
Response Codes
- 200 – Existing request is being reused. Existing request ID in the response body.
- 201 – Request successful. Request ID in the response body.
- 403 – User does not have permissions to request the indicated account or the account does not have API access enabled. Response body contains a status code indicating the reason for this forbidden access:
- 4031 – User does not have permission to request the account or the account is not valid for the system.
- 4033 – Approver Only API or account. Only Approvers can access this API or account.
- 4035 - Not enough Approvers configured to approve a request.
- 409 – Conflicting request exists. This user or another user has already requested a password for the specified account within the next <durationMinutes> window.
For more information, please see Common Response Codes.
PSRUN command:
psrun2 127.0.0.1 3ea6..acb5acc "cli;pwd=[Password1]" POST Requests SystemId=1 AccountId=12 DurationMinutes=30 Reason="Just to test request"