Walkthrough: Create a sudo GPO
You can create a GPO to specify a sudo configuration file for target computers. Sudo, or superuser do, allows a user to run a command as root or as another user. You can use this GPO to control sudo access in a centralized and uniform way.
The sudo configuration file is copied to the local computer and replaces the local sudoers file. A sudo file can reference Active Directory users and groups. For more information about sudo, see the man pages for your system.
When you define the GPO, you can also set its target platforms. The GPO settings are applied only to the operating systems, distributions, and versions that you choose.
The AD Bridge entries in your sudoers file must conform to the rules set in "Configure Entries in Your Sudoers Files" in the AD Bridge Administration Guide.
Create a sudo GPO
To create or edit a GPO, you must log on as a member of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security group.
- In the Group Policy Management Editor, expand either Computer Configuration or User Configuration, expand Policies > Unix and Linux Settings.
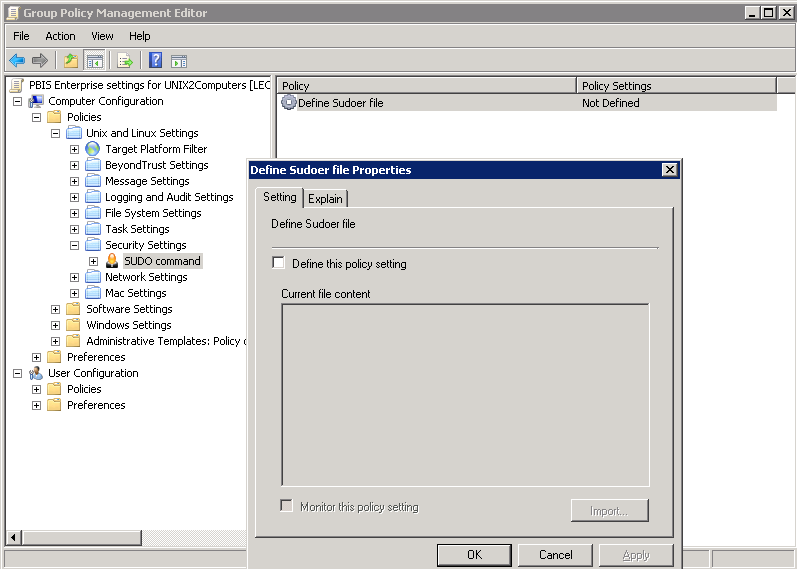
- Expand Security Settings, and then select SUDO command.
- Double-click Define Sudoer file.
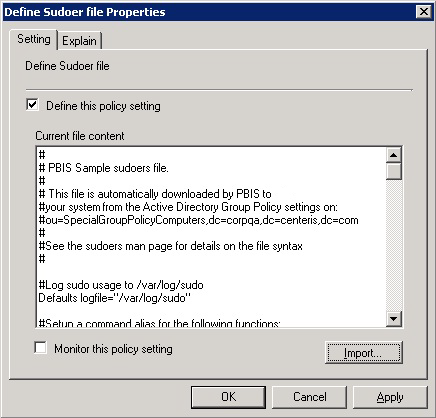
- Check the Define this Policy Setting box, and then in the Current file content box, type your commands. Or, to import a sudo configuration file, click Import.
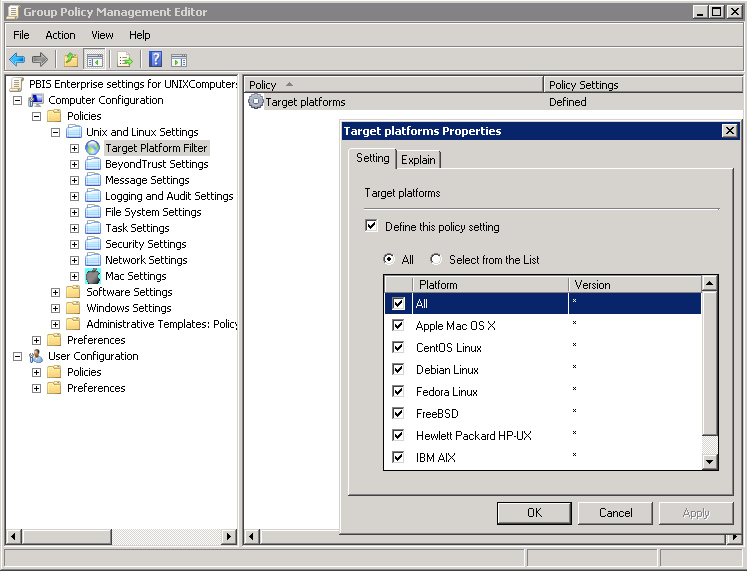
- Select Target Platform Filter.
- Double-click Target platforms.
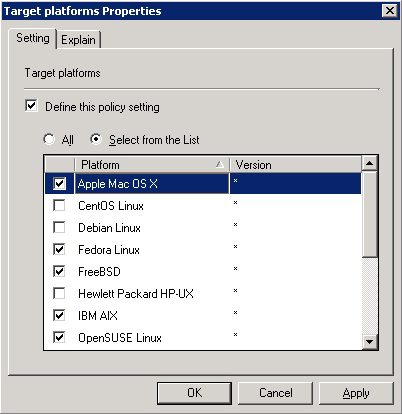
- To target all the platforms, select All. To choose platforms, click Select from the List, and then select the platforms.
Test the sudo GPO
After you set the sudo GPO, you can test it on a target computer. The target computer must be in a cell associated with the organizational unit where you linked the sudo GPO.
- On a target Linux or Unix computer, log on as an administrator and execute the following command to force AD Bridge Group Policy settings to refresh:
/opt/pbis/bin/gpupdate
- Check whether your sudoers file is on the computer:
cat /etc/sudoers
The location of the sudoers file varies by platform. For example, on Solaris it is in /opt/sfw/etc or /opt/csw/etc. On other platforms, it is in /usr/local/etc.
- Log on to the Unix or Linux computer as a regular user who has sudo privileges as specified in the sudoers configuration file.
- Try to access a system resource that requires root access using sudo. When prompted, use the password of the user you are logged on as, unless targetpw is set in the sudoers file. Verify that the user was authenticated and that the user can access the system resource.
Test sudo Security
- Log on as a user who is not enabled with sudo in the sudoers file that you used to set the Group Policy Object (GPO).
- Verify that the user cannot perform root functions using sudo with their Active Directory credentials.