Configure Syslog to Cull Events in AD Bridge
To collect sudo events and other system events that appear in syslog, you must configure syslog to write data to a location where the AD Bridge reapsysl service can find it and copy it to the local event log.
You can set an AD Bridge Group Policy setting to modify /etc/syslog.conf on target computers.
The reapsysl service creates three named pipes and picks up the syslog information written to them:
/var/lib/pbis/syslog-reaper/error /var/lib/pbis/syslog-reaper/warning /var/lib/pbis/syslog-reaper/information
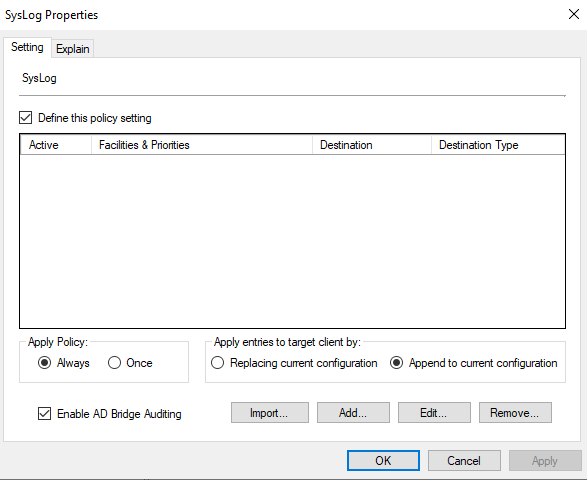
To configure event forwarding using policy settings:
- In the Group Policy Management Console, create a Group Policy Object (GPO) for an organizational unit, and then edit the OU in the Group Policy Management Editor.
- In the console tree, expand Computer Configuration > Policies > Unix and Linux Settings > BeyondTrust Settings > Logging and Auditing Settings, and then click SysLog.
- Double-click SysLog, and then check the Define this policy setting box.
- At the bottom left, check the Enable AD Bridge Auditing box.
- Click OK.
Additionally, these settings can be changed on the agent machine. To configure syslog to write to the pipes, add the following lines to /etc/syslog.conf:
*.err /var/lib/pbis/syslog-reaper/error *.warning /var/lib/pbis/syslog-reaper/warning *.debug /var/lib/pbis/syslog-reaper/information
The last entry is not analogous to the first two. Some versions of syslog require a tab character rather than spaces to separate the two components of each line.
After you modify syslog.conf, you must restart the syslog service for the changes to take effect:
/etc/init.d/syslog restart
systemctl restart syslog
For more information, see the following:
- AD Bridge GPO Reference Guide.
- Your syslog documentation.